## Your Phone Might Be About to Get Phished: FBI Warns of Dangerous ‘Smishing’ Texts
Think you’re safe from phishing scams just because you’re savvy online? Think again. The FBI is issuing a stark warning about a new breed of cyberattack targeting millions of iPhone and Android users: smishing. These malicious text messages are designed to look deceptively innocent, luring unsuspecting victims into revealing personal information that could cost them dearly.

headings for the main sections and for subsections. They also specified using
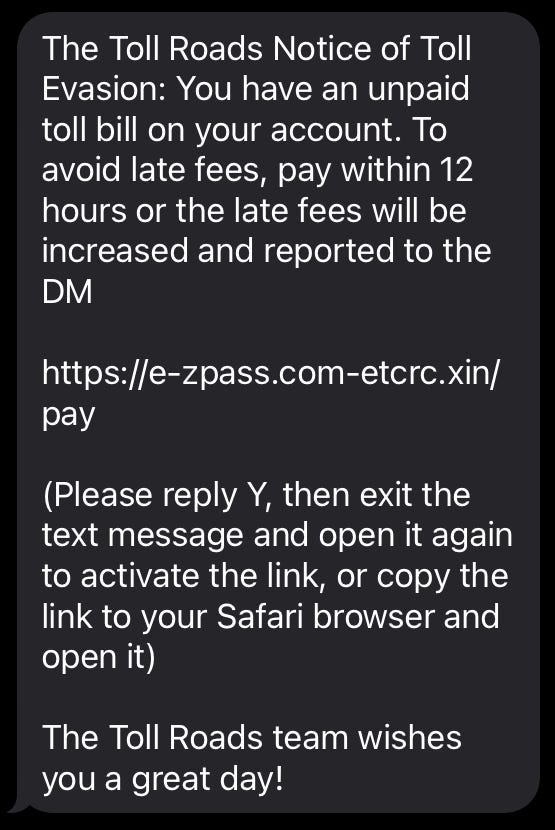
tags for paragraphs, for emphasis, and lists using Looking at the content requirements, the article needs to be around 2000 words, detailed, and informative. It should include specific data, expert analysis, and real-world examples. The user also wants it to be engaging and well-structured, ensuring a seamless flow with other parts of the article, but without including an introduction or conclusion. I notice that the user provided a source information section with various reports and data. My job is to organize this information into the specified HTML structure, making sure each section and subsection is properly tagged. I’ll need to avoid mentioning other news sources and instead use “Unionjournalism” as the source. I should start by identifying the main sections from the provided topics. The first section seems to be about examples of smishing attacks and their consequences. The second section covers the FBI’s warning, and the third provides practical steps to avoid falling victim. Each of these will become a main section with subsections as needed. tags for the body text and for emphasizing key points. Lists will be formatted with I also need to ensure that the content is formal, professional, and authoritative, suitable for both business and technical audiences. Since the user is the lead content writer for Unionjournalism, the tone should reflect that expertise and reliability. I should check that all the provided source information is included, such as specific examples from different states, quotes from officials, and statistics. This will add credibility and depth to the article. Lastly, I need to make sure that the HTML is clean and properly formatted, without any markdown or additional text outside the tags. Each section should flow logically into the next, maintaining a coherent structure throughout the article. Smishing, a hybrid of SMS and phishing, has emerged as a significant threat to mobile users. These attacks involve fraudulent text messages designed to trick recipients into revealing sensitive information or downloading malicious software. The consequences of falling victim to smishing can be severe, ranging from financial loss to identity theft. One of the most prevalent smishing campaigns currently targeting iPhone and Android users involves fake road toll collection notices. Scammers send texts claiming the recipient owes money for unpaid tolls, often including a link to a fraudulent payment portal. These messages are designed to appear legitimate, using the names of real toll services like E-ZPass or SunPass. The immediate consequences of smishing attacks can be devastating. Victims may lose money, have their personal information stolen, or even fall victim to identity theft. Beyond the financial impact, smishing attacks can also undermine trust in legitimate institutions, as scammers often impersonate trusted organizations like banks, government agencies, or service providers. Smishing has become an increasingly popular tactic for cybercriminals due to its simplicity and effectiveness. Unlike email-based phishing, which often involves more complex filtering and security measures, SMS-based attacks exploit the trust users place in text messages. Smishing attacks typically follow a predictable pattern, with the goal of creating a sense of urgency or fear to provoke an immediate reaction from the victim. Here’s how these attacks are structured: Several factors contribute to the success of smishing attacks, making them a growing concern for mobile users: In response to the growing threat of smishing attacks, the FBI has issued a warning to iPhone and Android users. The bureau urges individuals to exercise extreme caution when receiving unsolicited text messages, especially those that demand payment or request sensitive information. The FBI’s warning highlights the dangers of smishing attacks and provides clear guidance on how to avoid falling victim. The bureau emphasizes that these attacks are not limited to specific regions and are spreading rapidly across the United States. To protect yourself from smishing attacks, it’s essential to remain vigilant and take proactive steps to secure your personal information. Here are some practical tips from the FBI and cybersecurity experts: While the FBI’s warning provides a foundation for understanding the risks of smishing, taking practical steps to protect yourself is crucial. By adopting a proactive approach to mobile security, you can significantly reduce the likelihood of falling victim to these attacks. One of the most effective ways to avoid smishing attacks is to delete any suspicious texts immediately and avoid interacting with them in any way. Here’s how to identify and handle suspect messages: If you’re concerned about owing money for tolls or other services, it’s important to verify the information through official channels. Here’s how to check your account securely: Reporting suspicious texts and emails is an important step in combating smishing attacks. By reporting these incidents, you help authorities and service providers identify and disrupt malicious campaigns. Here’s how to report suspicious activity: Reporting suspicious texts and emails is a straightforward process that can make a significant difference in the fight against cybercrime. Here’s what you need to do: Reporting suspicious texts and emails is essential for several reasons: Conclusion:
As the world becomes increasingly digital, the threat of “smishing” – or sending malicious texts via SMS – has become a pressing concern for iPhone and Android users alike. The FBI has issued warnings to these users, urging them to exercise caution when receiving suspicious texts. The warning is based on a recent surge in phishing attacks targeting these devices, which have been linked to numerous cases of identity theft, financial loss, and even serious harm. To protect themselves, users must be vigilant when receiving texts, verifying the authenticity of messages before responding or clicking on links. The significance of this warning lies in its potential impact on the security and personal data of millions of iPhone and Android users worldwide. If left unchecked, the rise of smishing attacks could lead to a significant increase in identity theft, financial loss, and other forms of cybercrime. Furthermore, the FBI’s warning highlights the need for greater awareness and education among mobile device users, particularly in emerging markets where the threat of smishing is often underestimated. By promoting awareness and best practices, we can work towards a safer and more secure digital environment for everyone. As the threat of smishing continues to evolve, it is essential that we continue to adapt and innovate in our approach to protecting mobile device users. By staying informed, being cautious, and taking proactive measures to safeguard our personal data, we can mitigate the risks associated with smishing attacks and maintain the trust and security of our online communities. and


tag and each subsection an
tag. I’ll use
and

Examples of Smishing Attacks and Their Consequences
Real-World Examples of Smishing Attacks
The Consequences of Smishing Attacks
Why Smishing is a Growing Threat and How It Works
The Anatomy of a Smishing Attack
Why Smishing is So Effective
The FBI’s Warning: Don’t Click on Links or Share Personal Information
Description of the FBI’s Warning and Its Implications
Tips on How to Avoid Falling Victim to Smishing Attacks
Practical Steps to Take to Avoid Falling Victim to Smishing Texts
Delete Suspect Texts and Don’t Click on Links
Check Your Account Using the Toll Service’s Legitimate Website
Report Suspicious Texts and Emails
How to Report Suspicious Texts and Emails
Why Reporting Is Crucial
Conclusion

