Apple’s foray into the complex world of artificial intelligence is taking an unexpected turn, raising eyebrows in Washington. A recent agreement with Alibaba, the Chinese tech giant, has sparked a firestorm of concern, igniting a debate about national security and the balance of power in the tech arena.

Apple’s Strategic Partnership with Alibaba: Analyzing the Objectives and Scope
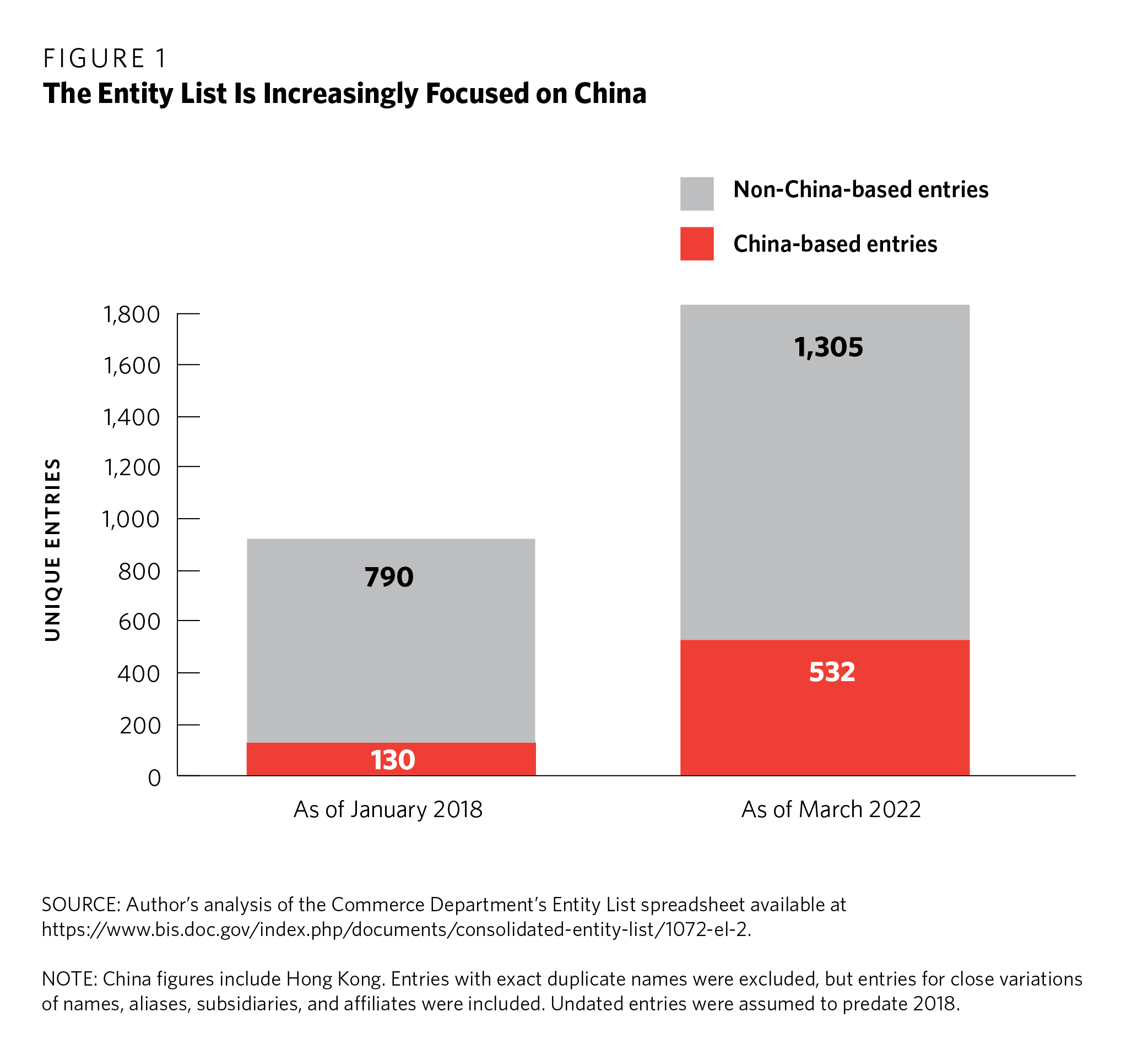
Apple’s recent agreement with Alibaba, a Chinese e-commerce giant, has triggered significant debate in Washington, highlighting the growing tension between US-China technological interdependence and national security concerns. While the specific terms of the deal remain partially undisclosed, analysts suggest it focuses on integrating Alibaba’s vast cloud computing infrastructure and AI capabilities into Apple’s product ecosystem. This collaboration could potentially revolutionize how Apple delivers services like Siri, Maps, and its App Store, leveraging Alibaba’s expertise in localized language processing and user experience within the Chinese market.
The strategic rationale behind this partnership is multifaceted. For Apple, gaining access to Alibaba’s robust infrastructure could alleviate pressure on its own servers, particularly as demand for its services surges in China, the world’s largest smartphone market. Alibaba, on the other hand, stands to benefit from Apple’s deep integration with global consumers and its brand cachet. This alliance could bolster Alibaba’s cloud computing ambitions and solidify its position as a leading AI platform in Asia.
A.I. Integration: How the Deal Could Shape the Future of Apple Products and Services
The partnership’s implications extend beyond infrastructure. Apple has long been an innovator in artificial intelligence, but its AI development has primarily focused on on-device processing, prioritizing user privacy. Alibaba, however, has adopted a more cloud-centric approach to AI, leveraging massive datasets to train sophisticated algorithms. By integrating Alibaba’s AI capabilities, Apple could potentially enhance the personalization and responsiveness of its products and services.

Potential Enhancements:
- Siri: Alibaba’s language processing expertise could significantly improve Siri’s accuracy and fluency in Mandarin and other Asian languages, expanding its utility for Chinese users.
- Maps: Integrating Alibaba’s data on local traffic patterns and points of interest could create a more dynamic and localized mapping experience for Apple users in China.
- App Store: Alibaba’s understanding of Chinese consumer preferences could help Apple curate a more relevant and engaging app store experience for its Chinese customer base.
Furthermore, this collaboration could pave the way for Apple to explore new AI-powered services in China, such as personalized shopping recommendations or localized content creation tools.
Potential Risks and Challenges: Navigating the Complexities of Data Privacy and Security
While the potential benefits of Apple’s partnership with Alibaba are substantial, several significant risks and challenges must be carefully considered. The most pressing concern is data privacy and security.
Data Privacy Concerns:
- Data Location: Storing user data on Alibaba’s servers raises concerns about its compliance with US data privacy regulations, particularly in light of China’s stringent data security laws.
- Data Access: There are anxieties that Chinese authorities could gain access to user data stored on Alibaba’s servers, potentially compromising user privacy and security.
- Data Sharing: The terms of the agreement regarding data sharing between Apple and Alibaba remain unclear. It is crucial to ensure that user data is not used for purposes beyond the scope of the partnership without explicit user consent.
Apple has a strong reputation for protecting user privacy and security. It faces a difficult balancing act in this partnership: leveraging Alibaba’s capabilities while maintaining its commitment to user data protection. The company must be transparent with its users about data handling practices and implement robust security measures to mitigate potential risks.
Security Vulnerabilities:
Integrating Alibaba’s systems with Apple’s ecosystem could create new vulnerabilities that malicious actors could exploit. It is essential that both companies conduct thorough security audits and implement robust safeguards to protect against cyberattacks and data breaches.
The US government has expressed concerns about the potential security risks associated with this partnership. The Committee on Foreign Investment in the United States (CFIUS) may review the deal to assess its national security implications.
National Security Concerns: Examining the US Government’s Fears of Technological Dependence
The U.S. government’s apprehension regarding technological interdependence with China stems from a deep-seated belief that Beijing possesses the capability to exploit these linkages for nefarious purposes. Washington harbors concerns that China could leverage these connections to pilfer sensitive information, disseminate disinformation, conduct surveillance on dissidents, seize control of critical U.S. infrastructure, and accelerate its economic ascendancy, among other potential threats.
These anxieties are not unfounded. China’s history of intellectual property theft, aggressive cyber espionage campaigns, and its propensity to utilize state-sponsored actors for economic and political gain have fueled a sense of unease in the U.S. government. The rapid advancements made by Chinese tech giants like Huawei and ZTE in areas such as 5G telecommunications and artificial intelligence have further intensified these concerns, as they could potentially create vulnerabilities in critical U.S. infrastructure and supply chains.
Potential Avenues of Exploitation
- Intellectual Property Theft: China has a long-standing history of intellectual property theft, with U.S. companies losing billions of dollars annually to counterfeiting and technology piracy. This poses a significant threat to American innovation and economic competitiveness.
- Cyber Espionage: Chinese state-sponsored cyber actors have been implicated in numerous high-profile breaches targeting U.S. government agencies, private companies, and research institutions. These attacks aim to steal sensitive data, intellectual property, and national security secrets.
- Surveillance and Censorship: The Chinese government utilizes sophisticated surveillance technologies to monitor its citizens and suppress dissent. The potential for these technologies to be exported and deployed elsewhere raises concerns about human rights violations and the erosion of privacy.
Political Pressure: The Role of Congressional Scrutiny and Public Opinion
The growing unease over China’s technological ambitions has translated into significant political pressure on the U.S. government to take a more assertive stance. Both Democrats and Republicans in Congress have expressed increasing alarm over the potential risks posed by China’s technological rise. This bipartisan consensus has led to a series of legislative initiatives aimed at curbing China’s access to sensitive technologies and strengthening U.S. technological competitiveness.
Congressional Actions
- The Committee on Foreign Investment in the United States (CFIUS): This interagency committee reviews foreign investments in U.S. companies to ensure they do not pose a national security threat. CFIUS has become more stringent in its scrutiny of Chinese investments, blocking several high-profile deals in recent years.
- The Export Control Reform Act of 2018: This law expands the U.S. government’s authority to control the export of sensitive technologies to foreign adversaries, including China. It includes measures to restrict the export of artificial intelligence, quantum computing, and other advanced technologies.
- The Secure Act and the US Innovation and Competition Act: These bipartisan bills seek to bolster U.S. technological competitiveness by investing in research and development, strengthening STEM education, and providing incentives for domestic manufacturing.
Public Sentiment
Public opinion in the U.S. has also shifted towards a more cautious approach towards China’s technological influence. Concerns about economic espionage, intellectual property theft, and the potential for Beijing to leverage its technological prowess for geopolitical gain have fueled a sense of apprehension among Americans. This growing public skepticism has put pressure on policymakers to take action.
The “Technological Decoupling” Narrative: Understanding the Broader Geopolitical Context
The concept of “technological decoupling” has emerged as a dominant narrative in the discourse surrounding U.S.-China relations. This term refers to the deliberate effort by governments and businesses to reduce their dependence on each other for critical technologies and supply chains. The rationale behind this decoupling is to mitigate the risks associated with technological interdependence, enhance national security, and protect economic interests.
The U.S. government has been at the forefront of this decoupling drive, imposing export controls, investment restrictions, and other measures to limit China’s access to advanced technologies. However, decoupling is not a unilateral phenomenon. China has also implemented its own restrictions on the flow of technology, particularly in sensitive areas such as artificial intelligence and quantum computing. Furthermore, other countries, particularly those in Europe and Asia, are increasingly taking a more cautious approach towards China’s technological ambitions, seeking to balance economic ties with national security concerns.
Motivations for Decoupling
- National Security: Governments are increasingly concerned about the potential for China to exploit technological interdependence for military and intelligence purposes. They view decoupling as a way to safeguard critical infrastructure, protect sensitive technologies, and reduce vulnerabilities to cyberattacks.
- Economic Competition: Decoupling is also driven by a desire to protect domestic industries and maintain economic competitiveness. By reducing reliance on China for critical technologies and supply chains, countries aim to foster innovation, create jobs, and secure their economic future.
- Values and Ideals: Some governments and businesses are motivated by a desire to align their technological choices with their values and ideals. They are concerned about the potential for China’s technological dominance to undermine human rights, freedom of expression, and democratic principles.
Conclusion
The recent partnership between Apple and Alibaba, a leading Chinese e-commerce company, has sparked intense resistance from Washington, as revealed in a recent expose by The New York Times. The deal, which involves the integration of Alibaba’s artificial intelligence technology with Apple’s ecosystem, has raised concerns among policymakers and experts about the potential risks and implications for national security and data privacy. Key arguments discussed in the article highlighted the fears of data exploitation, surveillance, and intellectual property theft, which could compromise the sensitive information of millions of users.
The significance of this deal cannot be overstated, as it represents a critical juncture in the ongoing debate about the intersection of technology, business, and national security. The implications of this partnership are far-reaching, with potential consequences for the global economy, international relations, and the future of technological innovation. As Washington continues to scrutinize the deal, the article underscores the need for greater transparency, regulation, and accountability in the rapidly evolving tech landscape.
As the dust settles on this contentious issue, one thing is clear: the stakes are higher than ever before. The fusion of AI, data, and commerce is rewriting the rules of the game, and policymakers must adapt swiftly to mitigate the risks and capitalize on the opportunities. The question on everyone’s mind is: will Washington’s resistance be sufficient to safeguard national interests, or will the allure of technological advancements and economic growth prevail, potentially compromising the very fabric of our digital society? The answer remains uncertain, but one thing is certain: the fate of our digital future hangs precariously in the balance.
